Hi
In this tutorial I show you how to run openldap docker container together with keycloak to do user federation
First the openldap stack I used with portainer :
version: '2'
services:
openldap:
image: osixia/openldap:1.5.0
container_name: openldap
environment:
LDAP_LOG_LEVEL: "256"
LDAP_ORGANISATION: "secureit"
LDAP_DOMAIN: "secure.it"
#LDAP_BASE_DN: ""
LDAP_ADMIN_PASSWORD: "secureit"
LDAP_CONFIG_PASSWORD: "secureit"
LDAP_READONLY_USER: "false"
#LDAP_READONLY_USER_USERNAME: "readonly"
#LDAP_READONLY_USER_PASSWORD: "readonly"
LDAP_RFC2307BIS_SCHEMA: "false"
LDAP_BACKEND: "mdb"
LDAP_TLS: "false"
#LDAP_TLS_CRT_FILENAME: "ldap.crt"
#LDAP_TLS_KEY_FILENAME: "ldap.key"
#LDAP_TLS_DH_PARAM_FILENAME: "dhparam.pem"
#LDAP_TLS_CA_CRT_FILENAME: "ca.crt"
#LDAP_TLS_ENFORCE: "false"
#LDAP_TLS_CIPHER_SUITE: "SECURE256:-VERS-SSL3.0"
#LDAP_TLS_VERIFY_CLIENT: "demand"
LDAP_REPLICATION: "false"
#LDAP_REPLICATION_CONFIG_SYNCPROV: 'binddn="cn=admin,cn=config" bindmethod=simple credentials="$$LDAP_CONFIG_PASSWORD" searchbase="cn=config" type=refreshAndPersist retry="60 +" timeout=1 starttls=critical'
#LDAP_REPLICATION_DB_SYNCPROV: 'binddn="cn=admin,$$LDAP_BASE_DN" bindmethod=simple credentials="$$LDAP_ADMIN_PASSWORD" searchbase="$$LDAP_BASE_DN" type=refreshAndPersist interval=00:00:00:10 retry="60 +" timeout=1 starttls=critical'
#LDAP_REPLICATION_HOSTS: "#PYTHON2BASH:['ldap://ldap.example.org','ldap://ldap2.example.org']"
KEEP_EXISTING_CONFIG: "false"
LDAP_REMOVE_CONFIG_AFTER_SETUP: "true"
LDAP_SSL_HELPER_PREFIX: "ldap"
tty: true
stdin_open: true
volumes:
- openldap_data:/var/lib/ldap
- openldap_slapd:/etc/ldap/slapd.d
- openldap_certs:/container/service/slapd/assets/certs/
ports:
- "389:389"
#- "636:636"
# For replication to work correctly, domainname and hostname must be
# set correctly so that "hostname"."domainname" equates to the
# fully-qualified domain name for the host.
domainname: "secure.it"
hostname: "ldap-server"
phpldapadmin:
image: osixia/phpldapadmin:latest
container_name: phpldapadmin
environment:
PHPLDAPADMIN_LDAP_HOSTS: "openldap"
PHPLDAPADMIN_HTTPS: "false"
ports:
- "9444:80"
depends_on:
- openldap
volumes:
openldap_data:
driver: local
openldap_slapd:
driver: local
openldap_certs:
driver: local
then the Keycloak stack I used for Keycloak + Postgres
version: '3'
volumes:
postgres_data:
driver: local
keycloak:
driver: local
services:
postgres:
image: postgres
container_name: KEYCLOAK-DB
restart: always
volumes:
- postgres_data:/var/lib/postgresql/data
environment:
POSTGRES_DB: keycloak
POSTGRES_USER: keycloak
POSTGRES_PASSWORD: keycloak
keycloak:
image: quay.io/keycloak/keycloak
container_name: KEYCLOAK
restart: always
ports:
- 9445:8080
environment:
KC_DB_URL: jdbc:postgresql://postgres/keycloak
KC_DB_PORT: 5432
KC_DB_DATABASE: keycloak
KC_DB_USER: keycloak
KC_DB_PASSWORD: keycloak
KEYCLOAK_ADMIN: admin
KEYCLOAK_ADMIN_PASSWORD: keycloak
KC_HTTP_ENABLED: "true"
KC_HTTPS_ENABLED: "false"
KC_PROXY: edge
KC_HOSTNAME_STRICT: "false"
entrypoint: ["/bin/sh", "-c", "/opt/keycloak/bin/kc.sh build --db postgres && /opt/keycloak/bin/kc.sh start --optimized"]
depends_on:
- postgres
Then in Keycloak :
Go to User Federation and add a new federation
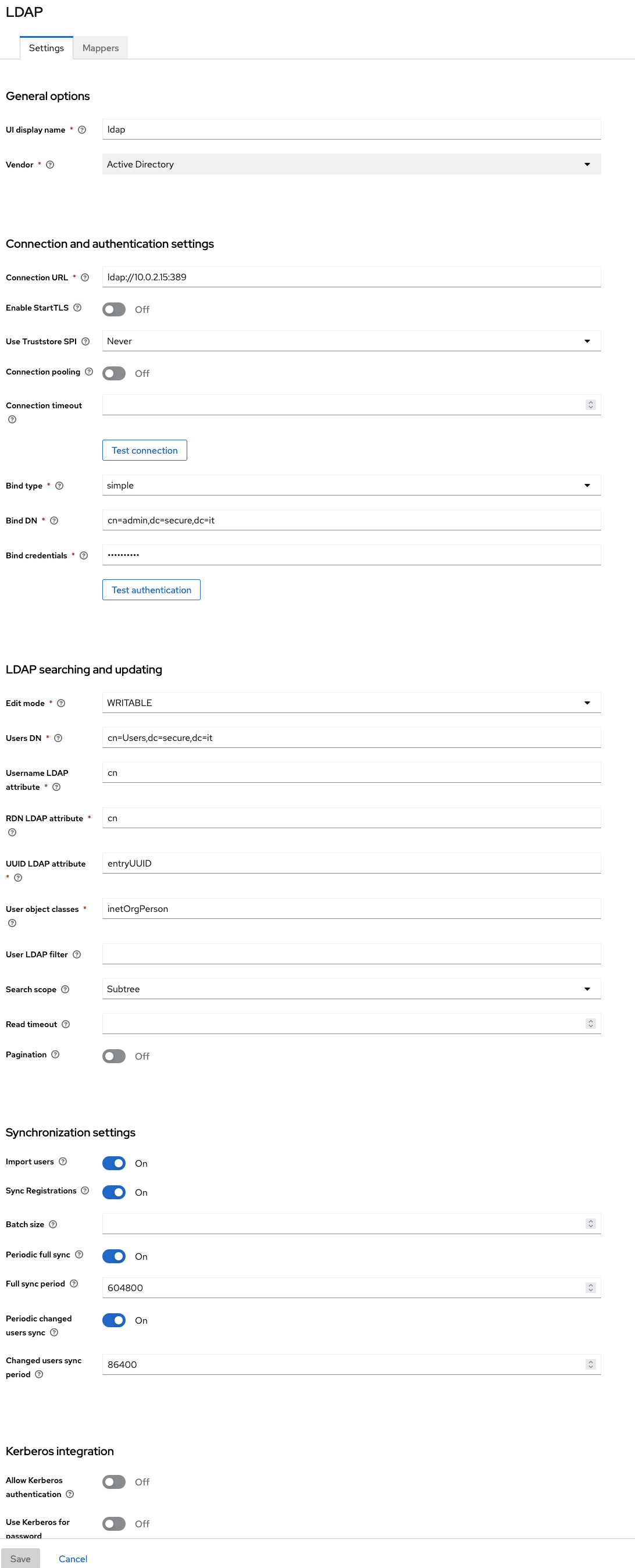
Update to synchronise users
Then go to Mappers and add a group mapper :
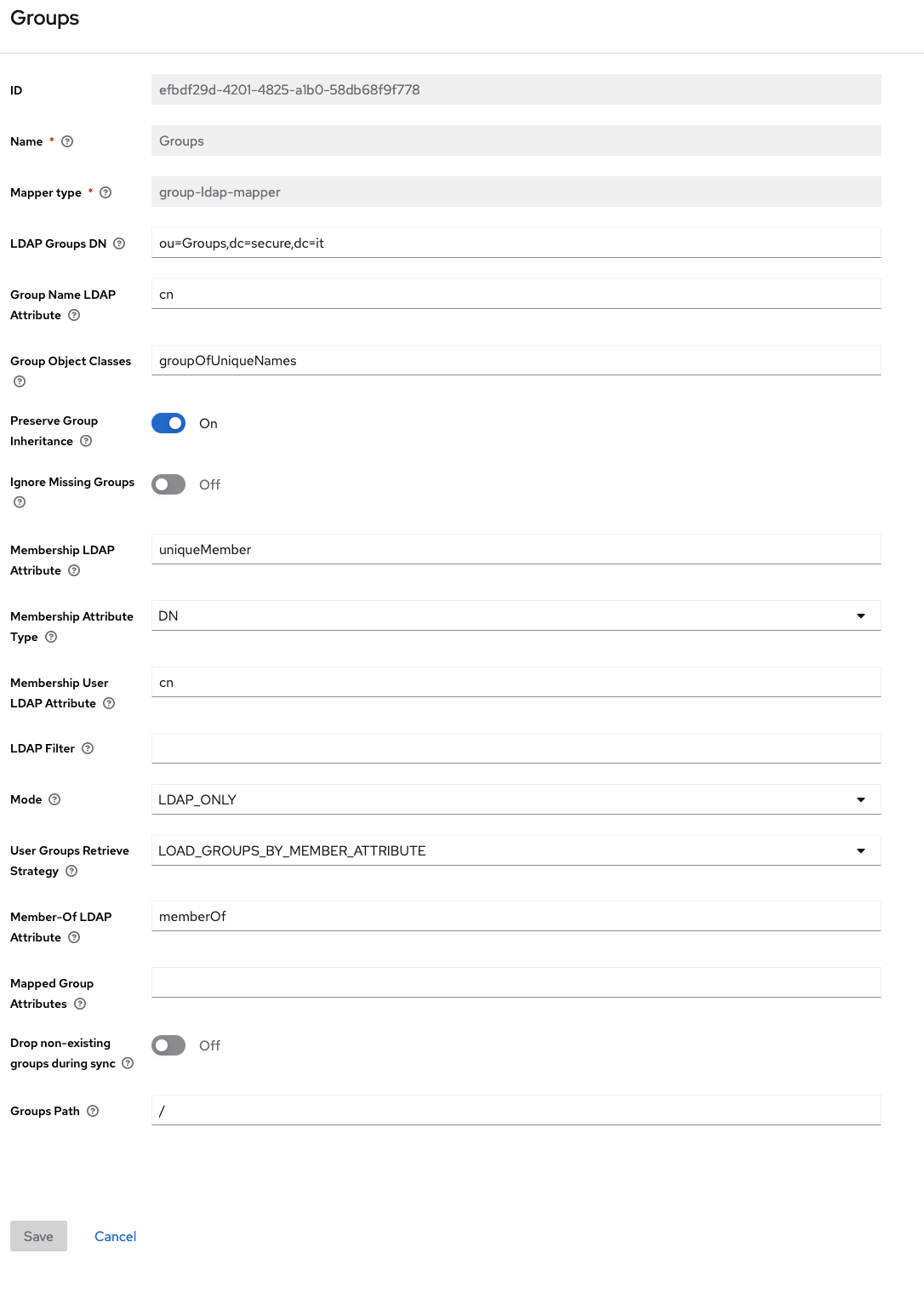
You're ready to go